Ovo je stara izmjena dokumenta!
Sažetak
Introduction
Log4j is a Java based logging tool developed by Apache and it is one of the most, if not the most popular logging tool available right now. Despite the careful testing and implementation of most available tools of wide varieties, security vulnerabilities rise up. These vulnerabilities are then logged via CVEs (Common Vulnerabilities and Exploits). Log4j is no such stranger to such vulnerabilities, having 8 vulnerabilities discovered from 2017 to 2021. However, on December 9, 2021, a 0-day exploit was discovered which allowed users to execute arbitrary code by exploiting the vulnerability. The vulnerability was described by some as the “the single biggest, most critical vulnerability of the last decade” and recieved a 10 out of 10 on the CVE severity scale labeling it as “critical”. It also recieved a name “Log4Shell”.
The exploit
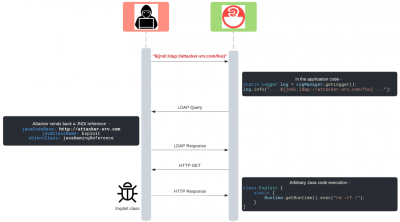
On December 9, 2021, a researcher from the Alibaba Cloud Security Team discovered an exploit targeting specifically the Log4j2 version of Log4j which could allow for arbitrary code execution and reported it to Apache. By default, Log4j supported a feature called Message Lookup Substitution which allows for specific strings to be replaced by other, dynamically created strings at runtime.
For example, logging the following string:
${java:runtime}
will yield a string similar to Java version 1.7.0_67 where the actual version would vary based on the version of Java the system was running. The researcher discovered that one of the lookup method, the JNDI lookup paired with the LDAP protocol will fetch a specified Java class from a remote source, deserialize it and execute it's code. JNDI stands for Java Naming and Directory Interface which provides naming and directory functionality to applications written using the Java programming language while LDAP stands for Lightweight Directory Access Protocol. This means that if any part of the logged string can be controlled by a remote attacker, the attacked gains remote code execution on the application that logged the string.
The exploit can be visualized via the following diagram:
Other exploits
Soon, a patch from Apache claiming to fix the exploit was released dubbed Log4j 2.15.0. However, not long after a new exploit was discovered against the users who had already downloaded the patch. The fix, as researchers said, was incomplete in certain non-default configurations and made it possible for attackers to perform certain Denial-of-service attacks prompting Apache to push out a third fix. Not long after, researchers at a security firm called Praetorian found an even more serious exploit which allowed data to be downloaded from the affected servers which prompted Apache to push out a third fix.
Praetorian also released a proof of concept(POC) demonstrating the exploit.